On Thursday morning, May 12, an IT expert who’s said to be monitoring the ongoing quick count of votes claimed that the data sent to the transparency server may have been altered.
The following screengrab shows how the IT expert confirmed that the hash codes of the files transmitted to the Comelec’s transparency server was possibly altered.
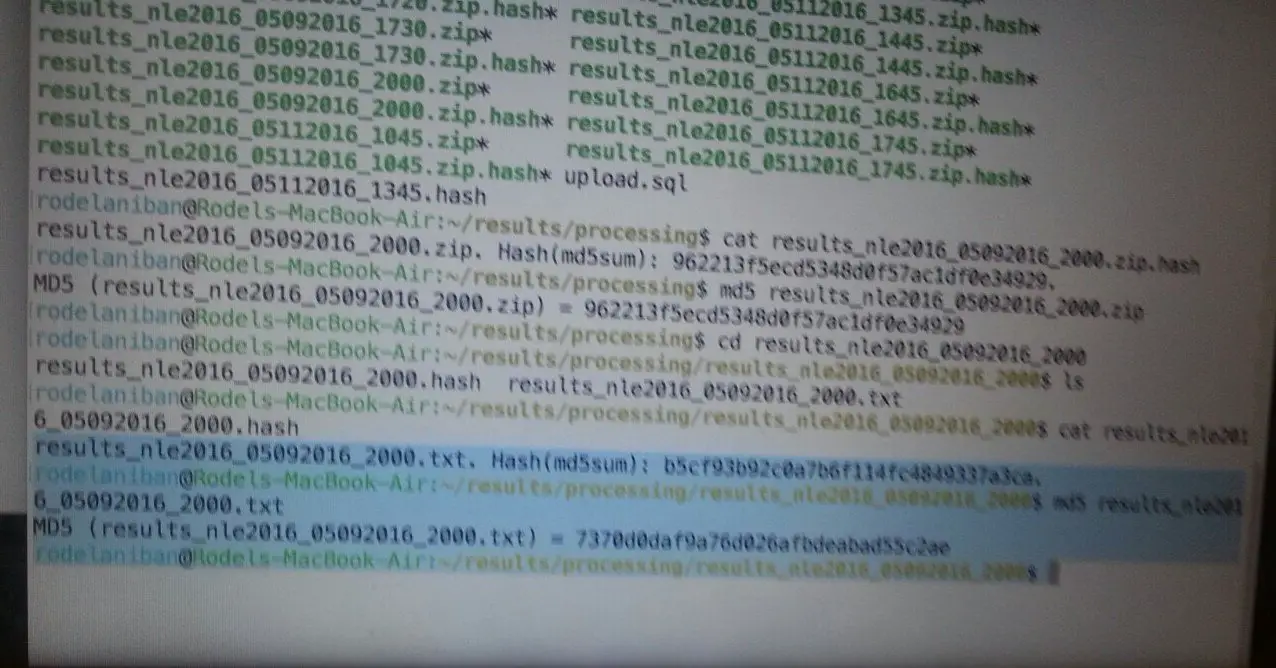
To give us a better outlook about what each command does, we started by typing the most relevant lines below.
rodelaniban@Rodels-Macbook-Air:~/results/processing$ cat results_nle2016_05092016_2000.zip.hashresults_nle2016_05092016_2000.zip. Hash(md5sum): 962213f5ecd5348d0f57ac1df0e0e4929.
rodelaniban@Rodels-Macbook-Air:~/results/processing$ md5 results_nle2016_05092016_2000.zipMD5 (results_nle2016_05092016_2000.zip): 962213f5ecd5348d0f57ac1df0e0e4929.
rodelaniban@Rodels-Macbook-Air:~/results/processing$ cd results_nle2016_05092016_2000rodelaniban@Rodels-Macbook-Air:~/results/processing/results_nle2016_05092016_2000$ lsresults_nle2016_05092016_2000.hash results_nle2016_05092016_2000.txt
rodelaniban@Rodels-Macbook-Air:~/results/processing/results_nle2016_05092016_2000$ cat results_nle2016_05092016_2000.hashresults_nle2016_05092016_2000.txt. Hash (md5sum): b5cf93b92c0a7b6f114fc4849337a3ca.
rodelaniban@Rodels-Macbook-Air:~/results/processing/results_nle2016_05092016_2000$ md5 results_nle2016_2000.txtMD5 (results_nle2016_05092016_2000.txt) = 7370d0daf9a76d026afbdeabad55c2ae
rodelaniban@Rodels-Macbook-Air:~/results/processing/results_nle2016_05092016_2000$So, how do we know what are the type of commands he’s using?
[ads1]
Linux Terminal Commands
At first glance, the lines of code presented above may be confusing, even dizzying, to anyone who doesn’t have an IT or programming background, particularly on Linux commands. To shed some light on these codes, we are going to dig further so you’ll understand the concepts better.
Assuming that you’re using Windows or MacOS PC, you can interact with your computer using a mouse and keyboard through a graphical user interface (GUI). An example of a GUI is your web browser (e.g. Chrome, Firefox, IE, Opera). Each action you perform on the GUI using the mouse (like clicking on the refresh button or pressing F5) executes a command. Basically, it’s a set of graphical icons and visual representation such as Windows.
On the other hand, Comelec-Smartmatic uses Linux systems. Comelec’s IT personnel interacts with the servers from their computers using the mouse and keyboard through a command-line terminal, which is a text-based interface using typed command labels or text navigation. The Linux command-line terminal also has an equivalent application in Windows PC known as the command/MS-DOS prompt.
From the screengrab above, we have re-written the code below appending line numbers before each command for easier reference and explanation later. The command on LINE 0001 generates an output or response that is printed on LINE 0002.
rodelaniban@Rodels-Macbook-Air:~/results/processing$ cat results_nle2016_05092016_2000.zip.hashLINE 0002: results_nle2016_05092016_2000.zip. Hash(md5sum): 962213f5ecd5348d0f57ac1df0e0e4929.
LINE 0003:
rodelaniban@Rodels-Macbook-Air:~/results/processing$ md5 results_nle2016_05092016_2000.zipLINE 0004: MD5 (results_nle2016_05092016_2000.zip): 962213f5ecd5348d0f57ac1df0e0e4929.
LINE 0005:
rodelaniban@Rodels-Macbook-Air:~/results/processing$ cd results_nle2016_05092016_2000LINE 0006:
rodelaniban@Rodels-Macbook-Air:~/results/processing/results_nle2016_05092016_2000$ lsLINE 0007: results_nle2016_05092016_2000.hash results_nle2016_05092016_2000.txt
LINE 0008:
rodelaniban@Rodels-Macbook-Air:~/results/processing/results_nle2016_05092016_2000$ cat results_nle2016_05092016_2000.hashLINE 0009: results_nle2016_05092016_2000.txt. Hash (md5sum): b5cf93b92c0a7b6f114fc4849337a3ca.
LINE 0010:
rodelaniban@Rodels-Macbook-Air:~/results/processing/results_nle2016_05092016_2000$ md5 results_nle2016_2000.txtLINE 0011: MD5 (results_nle2016_05092016_2000.txt) = 7370d0daf9a76d026afbdeabad55c2ae
LINE 0012:
rodelaniban@Rodels-Macbook-Air:~/results/processing/results_nle2016_05092016_2000$To interpret the set of commands, below are the terminal commands used:
- The “cat” command displays the contents of the file being called.
- The “md5” command runs an algorithm to verify the integrity of a downloaded file in the form of generated hash codes based on the contents of the file or package being called.
- The “cd” command allows the user to change or navigate to another directory such as a folder or a zipped file.
- The “ls” command allows the user to list the files and sub-directories of the current directory.
Digital Signatures
Each computer program, commonly known as software, always has “before” and “after” versions.
- a source code that is readable by humans; and,
- an object code or compiled file or the executable program readable by machines.
The source code consists of sets of programming statements created by a programmer with a text editor or visual programming tool and saved in a file. A compiler will be used to convert the source code into an executable computer program or object code.
The source code is the most important version of the program and for this reason, a compiled program often needs some later enhancements or debugging to fix issues.
In order to maintain the integrity of the executable program, a hash code will be generated using any form of hashing methods such as MD5, SHA-1 or SHA-256.
The hash code is a unique identifier of any computer program, also known as a digital fingerprint. This is also widely used by most software applications that can be downloaded on the Internet, to check whether the original files have been repackaged with malicious software or virus.
In the case of Comelec-Smartmatic, the source codes underwent a thorough review (The Review Process, The System, and Deployment) before it was compiled and deployed into the Vote Counting Machines (VCMs) to be usable. A single character change in the source code can also change the hash codes.
[ads2]
File/Folder Naming Structure
The strength of a folder and file naming convention is dependent on the specified naming structure and the quality and quantity of the data elements chosen to build it.
Complex hierarchical folder structures require extra browsing at time of storage and at the time of file retrieval. By having all the essential information concisely in the file name itself, both the search and identification of the file is streamlined and more precise.
Let’s take a look at the following line taken from the screengrab.
rodelaniban@Rodels-Macbook-Air:~/results/processing/results_nle2016_05092016_2000$The above line means, username@computername:~/directory/…/sub-directories$.
You may also have noticed that the file name is composed of this string “results_nle2016_05092016_2000“, which can be broken down into 4 elements as follows:
- results means Results
- nle2016 means National and Local Elections 2016
- 05092016 means May 09, 2016 (the date of when the file was created)
- 2000 means 8:00 PM (the 24-hour time-stamp format of when the file was created)
The file name can then be interpreted as “Results of the National and Local Elections 2016 on May 09, 2016 as of 8:00 PM”.
Hash Code Changed
Let’s discuss each line for you to understand what does each command mean.
rodelaniban@Rodels-Macbook-Air:~/results/processing$ cat results_nle2016_05092016_2000.zip.hashLINE 0002: results_nle2016_05092016_2000.zip. Hash(md5sum): 962213f5ecd5348d0f57ac1df0e0e4929.
The command on LINE 0001, “cat results_nle2016_05092016_2000.zip.hash”, instructs the computer to display the contents of the given file. It is expected to return the hash code of the .zip file it pairs with, which is 962213f5ecd5348d0f57ac1df0e0e4929.
rodelaniban@Rodels-Macbook-Air:~/results/processing$ md5 results_nle2016_05092016_2000.zipLINE 0004: MD5 (results_nle2016_05092016_2000.zip): 962213f5ecd5348d0f57ac1df0e0e4929.
The command on LINE 0003, “md5 results_nle2016_05092016_2000.zip”, tells the computer to run the md5 hashing algorithm on the given file. It is expected to output the same hash code as what’s returned on LINE 0002, which is 962213f5ecd5348d0f57ac1df0e0e4929.
rodelaniban@Rodels-Macbook-Air:~/results/processing$ cd results_nle2016_05092016_2000The command on LINE 0005 above, “cd results_nle2016_05092016_2000”, tells the computer to change its current directory, which you can see on LINE 0006 below.
rodelaniban@Rodels-Macbook-Air:~/results/processing/results_nle2016_05092016_2000$ lsLINE 0007: results_nle2016_05092016_2000.hash results_nle2016_05092016_2000.txt
The command on LINE 0006, “ls”, retrieves the list of files inside the current directory, which are printed out on LINE 0007.
rodelaniban@Rodels-Macbook-Air:~/results/processing/results_nle2016_05092016_2000$ cat results_nle2016_05092016_2000.hashLINE 0009: results_nle2016_05092016_2000.txt. Hash (md5sum): b5cf93b92c0a7b6f114fc4849337a3ca.
The command on LINE 0008, “cat results_nle2016_05092016_2000.hash”, instructs the computer to display the contents of the .hash file, which tells us on LINE 0009 that the .txt file should have a hash code equivalent to b5cf93b92c0a7b6f114fc4849337a3ca.
rodelaniban@Rodels-Macbook-Air:~/results/processing/results_nle2016_05092016_2000$ md5 results_nle2016_05092016_2000.txtLINE 0011: MD5 (results_nle2016_05092016_2000.txt) = 7370d0daf9a76d026afbdeabad55c2ae
The command on LINE 0010, “md5 results_nle2016_2000.txt”, generates a hash code of the text file that is printed on LINE 0011 which is 7370d0daf9a76d026afbdeabad55c2ae.
The Claim
The discrepancies in the hash codes is clearly visible at LINES 0008 and 0011. This is what the IT expert claimed to be the indicator that the transparency server has been compromised.
Marcos’ camp, through lawyer Francesca Huang, alleged on Wednesday, May 11, that a new script was introduced to the Transparency Server of the Commission on Elections (Comelec) “from which the PPCRV obtains its data for the quick count,” which “was able to alter the hash codes of the packet data” that could have boosted the votes of his rival, Leni Robredo.
But, is it really a valid claim? If it is, what could be the possible reasons and what are the files that can possibly be affected?
Comelec admits tweak
Comelec chief Andres Bautista on Thursday said that the tweaking of the script in the server meant only to replace a question mark (“?) to “ñ” in a candidate’s name, making sure that the integrity of poll results remain unaffected amid unproven claims of electoral fraud. The tallies remain unchanged, so no cheating was made underway to increase Robredo’s votes in any way. Comelec clarified that it was only a minor cosmetic change that did not affect the votes for any candidate.
Below is the screenshot of the written report on the inner Hash Code issue.

[50_50_first]

[/50_50_first][50_50_second]

[/50_50_second]
Comelec briefing
Watch the Comelec briefing about the script tweak below.
Basically, the script was only introduced to correct a character due to Unicode Transformation Format (UTF) encoding issues and it has nothing to do with the poll results.
For example, you are sending a text message with an emoji ” 🙂 ” to your friend using an iPhone. Your friend received the message through his Nokia phone and noticed that instead of seeing an emoji in the message, he’s seeing a “?”. So what does that mean?
That means that the older version of Nokia phones doesn’t understand and was not able to transform the emoji into its correct character encoding. Mainly, because the characters that transforms to emoji don’t exist in Nokia. Thus, displaying the “?” instead.
Be Informed. Beat the Trolls, Share the Truth!
[ads3]